Microsoft Windows 10 USB Forensic Artefacts
As the capacity of USB storage devices continues to increase and the price decreases, USB forensics will often play an important part in many forensic investigations.
Add to the mix a range of mobile devices such as smart phones, tablets, digital cameras and the ease of connectivity means that there are a lot of USB artefacts to be found if we know where to look.
For example in Windows 7, the Microsoft-Windows-DriverFrameworks-UserMode%4Operational.evtx log file contains useful information such as time stamps for the connection and disconnection of USB removable drives.
Many portable devices such as smart phones support the Media Transfer Protocol (MTP) and as a result we need to be looking in additional locations such as HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Portable Devices.
When the investigation involves USB devices the questions that often need to be answered include:
- What devices have been connected to the computer?
- When were the devices connected?
- Who connected the USB device to the computer?
- Was any data transferred to the USB device?
After returning from a trip to the UK in June this year and as a result of a discussion on USB artefacts with a former colleague, I felt inspired to do some research of my own. My aim was to create a portable tool that would collect the USB artefacts from all the different locations and present the results so the investigator can easily answer most of the above questions using just one tool. The result was a tool called USB Forensic Tracker.
I recently took the plunge and installed Windows 10 Professional on my laptop and I have to say I like it. I decided to take the opportunity to see if Windows 10 would offer any new locations where we may be able to recover USB artefacts. The main focus for this initial research was the log files within the following location: “C:\Windows\System32\winevt\Logs”.
Below are details of my initial findings:

- The content of my log file contained 199 entries. All of them were error level entries and related to USB devices that had been connected to my computer
- The entries included details of the USB devices including vendor details, model details, firmware version and serial number of the devices
- There is a time and date stamp for the entries that could be used to show when the devices were connected
- Entries appeared for USB removable pen drives, USB fixed hard drives and pen drives that appear as fixed drives
- Entries also appeared for my laptop internal hard drive
- No entries seem to appear in the log file for MPT devices
- The log entries also include a device number. When a USB device is connected it will be device number 1. If the first device is still connected when another USB device is connected, the second device will become device number 2 and so on.
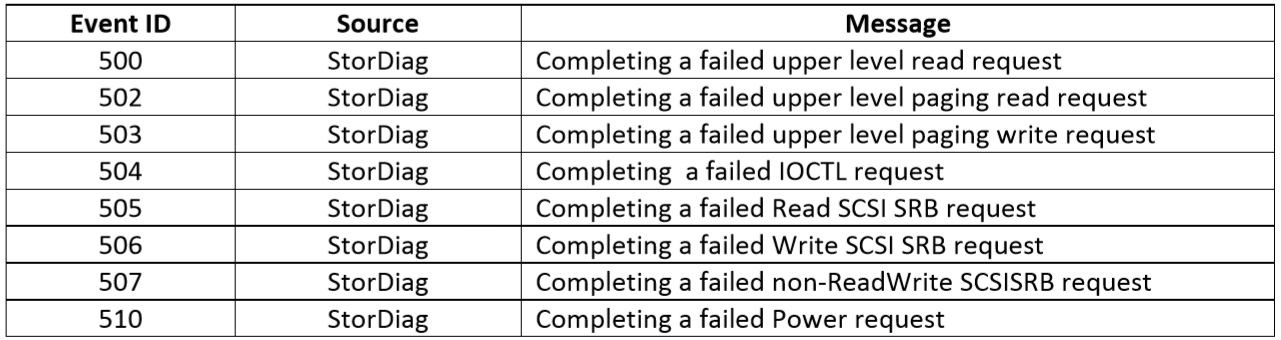
- Below are details of the Event ID’s found in the log file. The Event ID 507 was the most common one found followed by Event ID 504.
I also wanted to see if we could find evidence of MTP devices having been connected to the computer.
Below are details of my initial findings:

This log file was also present on Windows 7 but was not present on my Windows 8.1 test machine.
For my testing I used a Samsung Galaxy S5.
- Every time the device was connected to the computer, information entries were created in the log file.
- The entries provide a time and date stamp that can be used to show when a device was connected
- Unfortunately no details such as make or model of device are included in the log entries
- Below are details of the Event ID’s found in the log file.
USB Forensic Tracker has been updated to extract USB artefacts from the above locations.
About the Authors:
Mr. Andrew Smith (Andy) – Director of Computer Forensics Services at Orion Forensics Thailand
Andrew has 17 years’ experience in the field of digital forensics. Andrew was a UK police officer for 9 years of which the last 4 years was spent working within the police computer crime unit where he received extensive forensic training. His role included the acquisition of electronic data, analysis and the presentation of evidence in the UK courts as an expert witness.
Andrew has now been based in Bangkok for over 7 years and is the Director of Computer Forensics Services for a commercial investigation company called Orion Investigations. His role is to oversee all forensic investigations, business development, promote awareness of cyber security and present evidence as an expert witness in Thai courts. He has regularly appeared as a guest speaker for various business chambers and organizations. Andrew has developed a range of forensic training courses for the local Thai market. Andrew has also developed a number of free forensic tools which are now used in forensics labs all around the world.
Email: andrew@orioninv.co.th




