
Dealing with Cyber Crime – Would your business know how to respond
Dealing with Cyber Crime – Would your business know how to respond?
They say there are two certainties in life, death and taxes. I would suggest that there are now three. Death, taxes and being confronted with cybercrime.
It is not uncommon to hear the phrase cybercrime or cyberterrorism being used in the media and how another major company has been hacked. Yet many people are still unsure exactly what constitutes cybercrime and whether they may have been a victim.
Symantec defines cybercrime as “any crime that is committed using a computer or network, or hardware device. The computer or device may be the agent of the crime, the facilitator of the crime, or the target of the crime. The crime may take place on the computer alone or in addition to other locations”.
The term cybercrime covers a broad range of activity from spam emails, phishing emails (made to look like it originates from a legitimate company), identity theft, cyber harassment, illegal downloading of music, the hacking of networks and theft of company data.
Many businesses see spam emails more as an annoyance than a major threat. However it only takes one employee to click on a link that then redirects them to a malicious website. The website then covertly downloads and installs malicious software onto the system and then before you know it, all of your company’s data has been lost.
Businesses have a legal and moral obligation to protect their customer’s personal information. However, data leakage remains one of the biggest problems they face in todays’ technological world. A survey was conducted in 2012 by the National Cyber Security Alliance (NCSA) and Symantec of 1,000 small and medium-sized businesses (SMB). Some of the findings include the following:
- 87% of businesses do not have a formal written Internet security policy for employees.
- Nearly six out of 10 (59%) SMBs do not have a contingency plan outlining procedures for responding and reporting data breach losses.
- 75% of SMBs do not have policies for employee social media use on the job.
- 60% of SMBs say they do not have a privacy policy that employees must comply with when they handle customer or employee information.
Many SMB’s underestimate the seriousness of cybercrime or perceive trying to prevent becoming a victim as too difficult to deal with so ignore the problem. Hackers and others malicious users are well aware of this and as a result SMB’s are now a prime target.
So what are some of the emerging threats for 2013?
- Bring your own device (BYOD). The convergence of communication devices and technology is unprecedented and presents unique challenges for all businesses. People are now using mobile devices like they would a PC. It is estimated that by 2014 mobile Internet will overtake desktop Internet usage. The devices store large amounts of company data which can be automatically synced to various online storage locations. At a recent presentation I ascertained that most of the audience all had smart phones. However, when I asked how many had anti-virus installed on their phone only two put their hands up. According to a report by NQ Mobile, nearly 33 million android phones were targeted by malicious software in 2012.
- Social engineering – Many attackers now target social media websites such as Facebook or LinkedIn to gather intelligence about the company and the employees. These types of sites can be a rich source of information yet many companies still do not monitor what employees place onto the websites.
- Phishing continues to be one of the biggest threats to online privacy & security. Phishing is the practice of sending emails purporting to be from legitimate companies in order to induce individuals to reveal personal information such as passwords and usernames.
- Some of the biggest threats to a business continue to be from inside the company. It has been found that privileged users often get away with fraud for up to 32 months. When a business becomes a victim of cybercrime it can leave the organisation in a vulnerable position, ethically, financially and legally. All incidents need to be treated seriously. What starts out initially as an internal investigation could quickly expand into a criminal investigation which then involves outside agencies or the investigation could leak out to the public or the media.
The company will often turn to their IT staff to begin the investigation and the examination of computers and network to identify what has taken place. The problem is IT staff often have not received any training in the correct handling of electronic data that may be relied upon in court at a later data. Incorrect handling of electronic data could cause the integrity of the data to be called into question at court or disallowed altogether.
This is where digital forensics can assist. Digital forensics is the examination of electronic data stored on computers and other digital storage devices for evidence using approved methods that will cause no changes to occur to the data or minimal changes.
The range of devices that can be examined includes items such as computers, laptops, iPads, mobile phones, Satellite navigation systems, games consoles, printers, CD’s and DVD’s. Basically anything that stores electronic data.
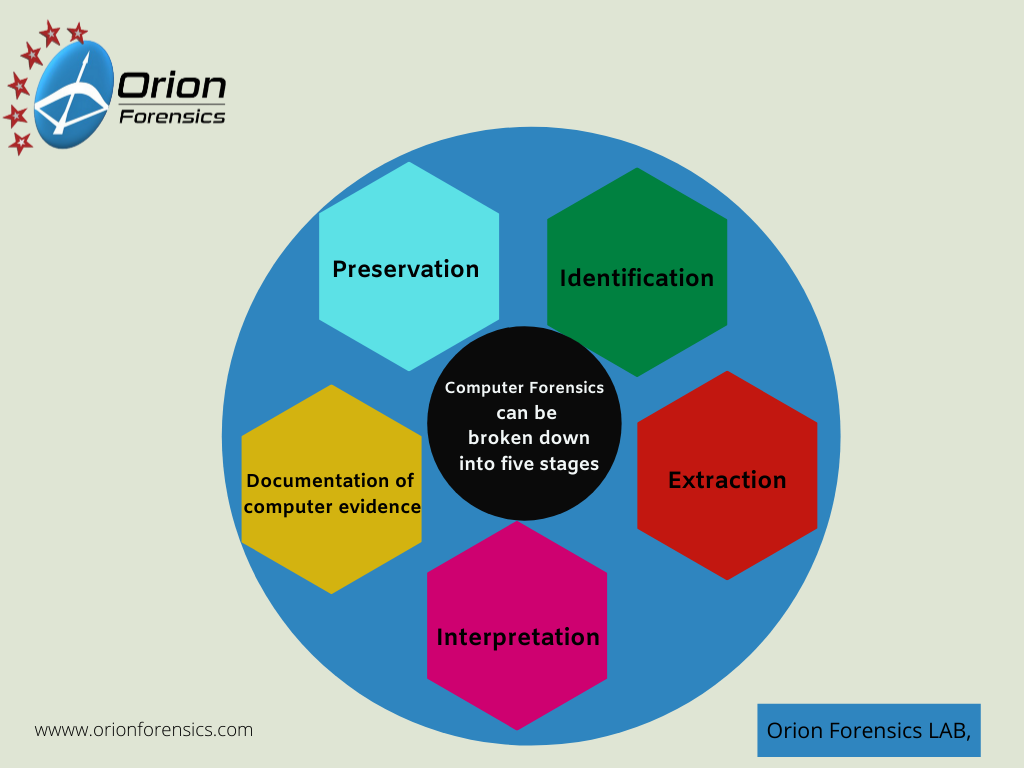
When a forensic investigation is conducted, there are 5 stages that the investigator will go through.
1. Preservation – the data will be preserved in such a way that no changes will occur to the data and as a result ensure the integrity of the data.
2. Identification – The volume of data that may need to be examined is increasing all the time. By conducting keyword searches the volume of data can be quickly reduced.
3. Extraction – It is vital that the data is extracted in a way that it can be demonstrated to the courts that the integrity and authenticity of the data has been maintained.
4. Interpretation – This is one of the most difficult areas of forensics and replies on the skills and experience of the investigator to be able to correctly interpret the data that has been found and the sequence of events surrounding that data.
5. Reporting – It is important to factually present the findings of the investigation but in a way that is not too technical and in an easy to read format.
When confronted with a forensic investigation, businesses initially tend to focus on the costs involved. Yes there is an up- front cost and depending on the complexity of the investigation and the number of computers involved, it can appear to be expensive. However consider the following:
- Evidence that can only be obtained by a forensic examination can often prove vital to the successful outcome of the investigation.
- A forensic investigation can often reduce the need for full legal action to be taken.
- A forensic investigation can save time resulting in a saving of money.
You have to consider how much it is costing your business to have your confidential information sold onto a competitor or the damage that may occur to your reputation if your client’s details have been stolen.
When I speak to people about what we can recover from computers or mobile phones they are often amazed. The types of data that can be recovered includes but is not limited to:
- Deleted data
- Documents
- Emails
- Images
- Internet history
- Instant chat conversations such as Facebook or Skype
- Details of files placed onto USB devices.
For mobile phones it also includes deleted call logs, deleted SMS messages and even location information such as GPS fixes. There is no doubt that businesses’ dependence on technology will continue to increase. Many are quick to adopt new technologies as a way to deliver their services quickly and cost effectively to their customers. The upsurge of the use of mobile devices means staff are no longer bound to a desk. However the use of such devices brings many challenges.
Although businesses are quick to adopt these technologies many either do not give sufficient thought to how to secure these devices or simply do not understand the potential for disaster. They need to not only look at how to prevent a cyber-security incident from occurring but have in place clear procedures for dealing with an incident when things do go wrong.
Digital forensics is a useful tool in the fight against cybercrime and if used correctly and early in the investigation may prevent vital information from being lost or destroyed.
For information regarding this subject please contact Andrew Smith | 089-926-8873 | andrew@orioninv.co.th
Author : Andrew Smith – Director of Computer Forensics ,Orion Investigations.
Published : http://www.bangkokbusinessbrief.com
About the Authors:
Mr. Andrew Smith (Andy) – Director of Computer Forensics Services at Orion Forensics Thailand
Andrew has 17 years’ experience in the field of digital forensics. Andrew was a UK police officer for 9 years of which the last 4 years was spent working within the police computer crime unit where he received extensive forensic training. His role included the acquisition of electronic data, analysis and the presentation of evidence in the UK courts as an expert witness.
Andrew has now been based in Bangkok for over 7 years and is the Director of Computer Forensics Services for a commercial investigation company called Orion Investigations. His role is to oversee all forensic investigations, business development, promote awareness of cyber security and present evidence as an expert witness in Thai courts.
He has regularly appeared as a guest speaker for various business chambers and organizations. Andrew has developed a range of forensic training courses for the local Thai market. Andrew has also developed a number of free forensic tools which are now used in forensics labs all around the world.
Email: andrew@orioninv.co.th



