
Keeping your Cryptocurrencies Safe

With cryptocurrencies such as Bitcoin, Ethereum and various alt coins having reached all-time highs recently, this has resulted in a flood of new investors opening trading accounts with crypto exchanges around the world. Many of these investors blinded by the potential for large profits may only have a basic level of knowledge of the crypto markets and how the underlying technology works. This results in many people falling prey to scammers, losing their investment on exchanges that perform exit scams or making mistakes that result in them losing access to their crypto forever.
With the renewed interest in cryptocurrencies, now seems like an appropriate time to discuss the steps you need to take to keep your cryptocurrencies safe. There is a popular saying in the crypto world, “Not Your Keys, Not Your Coins”. The saying refers to the need to owning the private keys associated with your crypto. Whoever controls the private keys ultimately controls the crypto. When someone sends you some cryptocurrency such as Bitcoin you will provide them with a receiving address. The exact format of the receiving address will vary from cryptocurrency to cryptocurrency. The receiving address is your public key. It is called a public key because you can send it to anyone without compromising your cryptocurrency. Associated with the public key is a private key. The private key is what allows you to access and control your cryptocurrency. The private key identifies you as the owner of the crypto and allows you to transfer or sell your crypto asset.
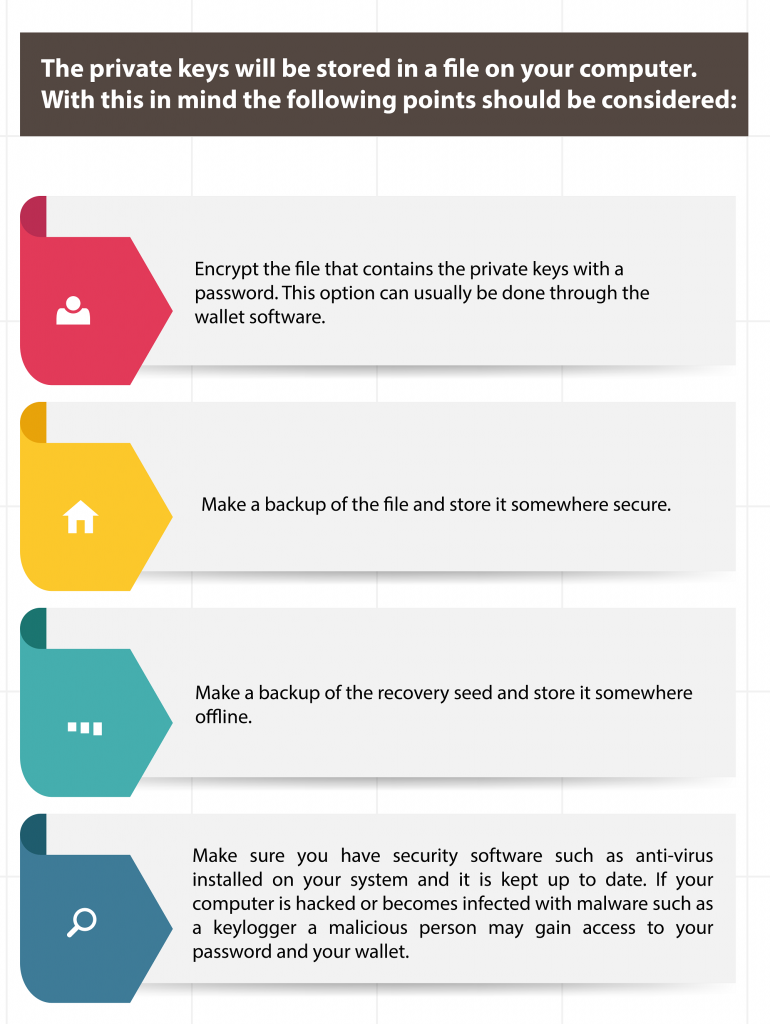
When you store your cryptocurrencies on an exchange, the exchange is in control of the private keys and as a result while you may have access to your crypto assets you do not have control of them. With this is mind the following points should be considered when using a crypto exchange:
- Only use well known reputable exchanges
- Only use exchanges that offer security features such as:
- Two-factor authentication (2FA), such as Google Authenticator
- Complex captchas
- Additional verification via email or SMS when logging in from new devices or IP addresses
- Only use exchanges that are insured in the event that they suffer a major hack.
- Use exchanges that store the majority of the crypto assets in cold wallets. A cold wallet is a wallet that is not connected to the Internet.
- Only use exchanges that undertake yearly security assessments by independent cyber-security firms.
- Only store on the exchange the crypto that you are actively trading.
- Do not use the exchange for long term storage of your crypto assets.
When not storing your cryptocurrency on an exchange, what options do you have to safely store your crypto? There are basically two category of wallets that you can use, hot wallets and cold wallets. A hot wallet is any wallet that is connected to the internet while a cold wallet remains disconnected from the Internet for the majority of the time.
Before I discuss the different types of wallets in more detail there is one misconception that needs to be cleared up. People often mistakenly think that their cryptocurrencies is stored in the wallet. This is not the case. The cryptocurrency remains located on the public blockchain while the wallet stores the information required to access the blockchain thereby allowing the user to conduct transactions. Information held on the wallet includes the public and private keys.
So how are the private keys generated? When you create a wallet where you have control of the keys, private keys will need to be created. This will generally be done by using something called a recovery seed. The seed will often consist of a list of either 12 or 24 random words which is used to generate the private keys. You will then create a password for access to the wallet. It is vital that you retain a copy of the recovery seed and keep the copy somewhere secure. If you ever forget your password the recovery seed can be used to regain access to your crypto. If someone else gains access to your recovery seed, they will also be able to gain access to your crypto and will be able to transfer it to a wallet under their control. It is recommended to write down your recovery seed on paper and keep it somewhere safe so it cannot be accessed via the Internet. Remember if you forget your password and lose your recovery seed it will be impossible to recover your cryptocurrency.
Hot Wallets
Hot wallets offer convenience and include exchange wallets, web wallets or software wallets installed on the computer or on mobile devices.
Web Wallets – A web wallet allows you to access your cryptocurrency via a web browser interface. You would create a wallet and a password to secure the wallet. However, it is important to understand that depending on the provider, they may still control the public and private key. Many web wallets do allow you to control the keys and the safest way to do this is to store your private keys on a hardware wallet (see further details on hardware wallet under cold wallets section). This option would give you full control over your keys in the most secure way. Therefore, it is important that you do your research before entrusting your cryptocurrency to a web wallet provider.
Software Wallets – Using a software wallet allows you to download and install the wallet to your computer or mobile devices. The advantage of a software wallet is that it gives you complete control of your private keys.
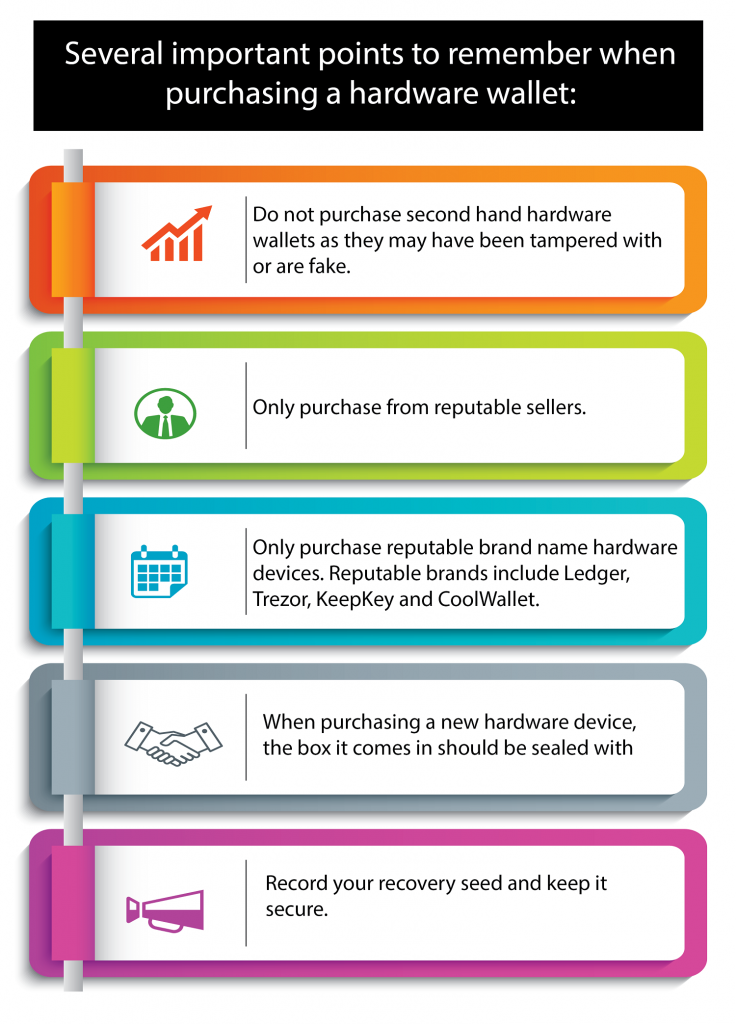
Hardware Wallets – hardware wallets are USB hardware devices that are used to generate public and private keys which are stored on the device itself. The hardware wallet is considered one of the most secure options for protecting your private keys. The device itself is protected by a password which you create and must enter in order to access the device. When you set up the device you will be provided with a recovery seed which as discussed before you must record and keep secure. The private keys for your web wallets and software wallets can be stored on the device. This means that when you wish to access your wallets the device must be plugged into your computer or connected via Bluetooth. A question commonly asked by people is “What happens if my hardware wallet breaks or is lost or stolen?” As long as you still retain possession of your recovery seed then there is no issue in regaining access to your crypto. It is simply a matter of obtaining a new hardware wallet and set it up using your recovery seed. You will then have full access to your cryptocurrency again.
Summary
The cryptocurrency market is highly volatile. Some crypto coins/tokens you currently own that are only worth a few cents each, may be worth thousands of dollars in a few years’ time. It is not uncommon to hear stories of people who forgot that they were storing cryptocurrency on their computer and as a result either reinstalled the operating system, sold the computer or simply forgot their password and as a result can no longer get access to their cryptocurrency that would have made them a millionaire.
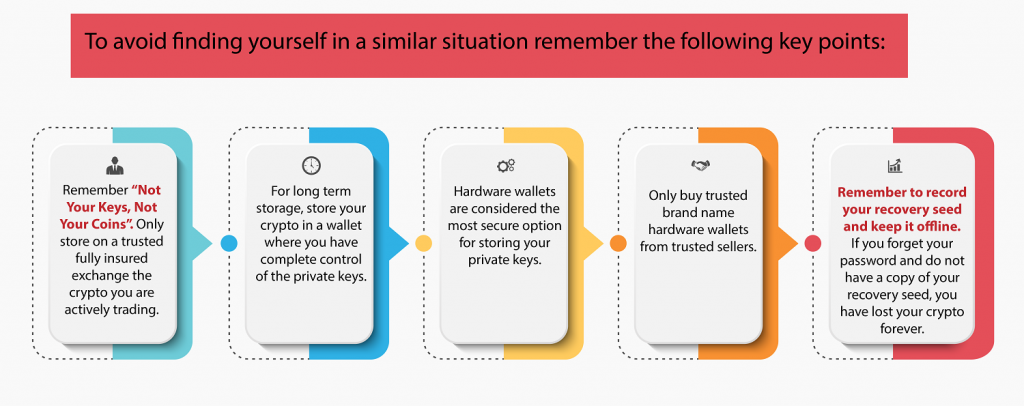
The final point to remember is that no customer service agent from a legitimate crypto exchange or wallet provider will ask you to provide them with your wallet password or recovery seed. If someone asks you for this information, they are trying to scam you.
“If you find yourself in the unfortunate position of having lost access to your cryptocurrency, either as a result of having forgotten your password or accidently deleting your wallet, then contact Orion to discuss how we may be able to assist.”
About the Author – Andrew has completed the CSITech Ltd Cryptocurrencies for Investigators course and is an active trader of various cryptocurrencies. He is not associated with any product brands mentioned in this article.
Read MoreDIGITAL DETECTION
When people hear the phrase “computer forensics”, they often think of the television program “CSI” and police criminal investigations. However computer forensics, or digital forensics as it is now commonly called, is an invaluable tool used in a wide range of investigations including contractual disputes between companies, employee misuse of computers, intellectual property investigations, computer hacking investigations and libel cases.
Read MoreOrion Forensics LAB Signed MOU with Korat Institute of Technology and Enterprise (KITE)
Andrew Smith- Director of Computer Forensics at Orion Forensics Lab has signed a Memorandum of Understanding (MOU) with Mr.Muhamad Arshad from Korat Institute of Technology and Enterprise (KITE) ,Thailand On September 14,2020
The purpose of this MOU is for co-branded training programs for entry-level cyber-crime investigators in Pakistan and elsewhere .





All digital Forensics training course CLICK
Read More
Required Skills for Digital Forensics Investigators
I have been a full time digital forensic investigator now for almost 15 years. I still remember the excitement on my first day when I started within the South Yorkshire Police Computer Crime unit. The learning curve was steep. I had no university degree in computers, limited computer training and most of what I knew about computers was self-taught including how to build computer systems.
Read MoreWhy is Digital Forensics Important to your Organization?
In today’s fast paced world, organisations have to rely more and more heavily on technology to remain competitive. Customers have come to expect organisations to have an online presence with professional looking websites, be able to respond quickly to online enquiries, have online chat functionality and have the ability to order online.
Read MoreWhat is Digital Forensics ?
What is Digital Forensics ? Digital forensics is the examination of electronic data stored on computers and other digital storage devices for evidence
Read More
Making Sense of Electronic Evidence (Avoiding the common mistakes)
I have been based in Bangkok now for the past 7 years and, with the push for a digital economy, Thailand 4.0 has meant that the issue of cyber-security has been pushed to the forefront. Each year we continue to see a growth in demand for forensic awareness training and for forensic examinations. However, there is still a general lack of understanding about digital forensics and we continue to see companies making the same mistakes over and over again.
Electronic data is fragile, if there is any chance it may be used as evidence in legal proceedings, then it must be handled in a certain way so it is possible to demonstrate to the court that the integrity and authenticity of the evidence has been maintained. If mishandled, then the evidence may be called into question when presented at court.

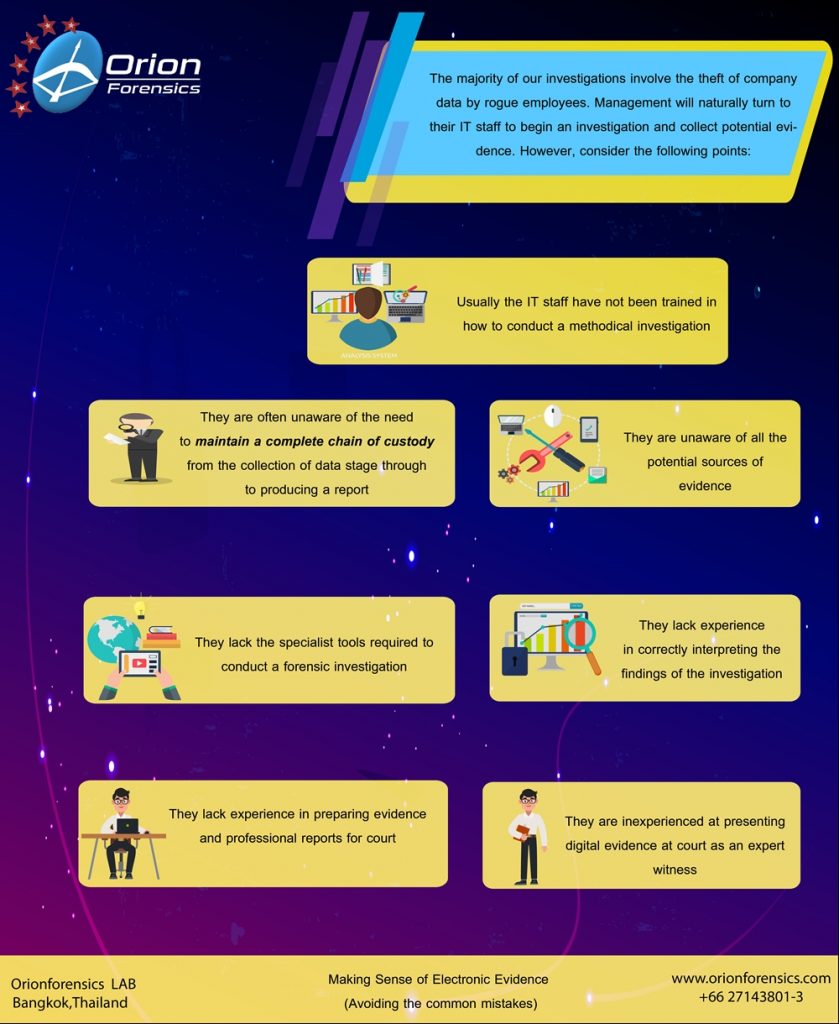
The majority of our investigations involve the theft of company data by rogue employees. Management will naturally turn to their IT staff to begin an investigation and collect potential evidence. However, consider the following points:
- Usually the IT staff have not been trained in how to conduct a methodical investigation
- They are often unaware of the need to maintain a complete chain of custody from the collection of data stage through to producing a report
- They are unaware of all the potential sources of evidence
- They lack the specialist tools required to conduct a forensic investigation
- They lack experience in correctly interpreting the findings of the investigation
- They lack experience in preparing evidence and professional reports for court
- They are inexperienced at presenting digital evidence at court as an expert witness
Companies often assume that as long as the person conducting the investigation holds some type of IT qualification then this will be sufficient. Digital forensics is a highly specialized field and, as demonstrated by the points above, requires a forensic investigator with the qualifications and experience to conduct the forensic investigation.
Another important issue to consider is the experience of your legal team. Do they have experience of dealing with cyber-crime cases and do they have the technical understanding of digital evidence? Due to the potential complexity of cyber-crime cases the legal team will often have to work closely with the forensic investigator to ensure the best possible outcome in any legal proceedings.
Without doubt the number of legal cases using electronic evidence will continue to grow. Also, as the number of forensic specialists in Thailand increases, we can expect to see electronic evidence that has not been handled correctly being more robustly challenged in the courts. If you are involved in legal proceedings where the other side is presenting digital evidence, you should consider hiring your own forensic expert to examine the validity of their evidence. In order to give yourself the best chance of success in any legal proceedings, make sure you use suitably trained forensic investigators and lawyers with the experience of dealing with electronic evidence.

My colleague Andrew was keen to get my perspective as a lawyer. Here it is.
As a young criminal defense lawyer a senior colleague advised me that the only way to succeed, whether you are prosecuting or defending, is to put all your energy into preparing your case for trial and most importantly, to “know and understand the subject matter”. Back then it was reasonably straight forward to understand the subject matter of the criminal charges before you. Today it’s a very different story indeed.
Technology has developed at an exponential rate in the last decade or so and has given rise to a far more sophisticated medium for the dishonest perpetrator to cause damage to the unsuspecting victim, be that an employer, a business, a bank, the Authorities or even another individual.
The motive of the crime can be to damage the reputation of the victim, unlawfully obtain the victim’s confidential information or fraudulently acquire cash or other assets belonging to the victim.
As a lawyer prosecuting or defending such a case the task of knowing and understanding the subject matter of your cybercrime case is an extremely difficult one. After all you are a lawyer and not a trained scientist. This is where you need to work alongside an expert with digital forensics training and experience.
As Andrew mentions above, lawyers and other prosecuting Authorities will often rely on persons who have some level of IT training to try and make sense of the data. This is where mistakes can occur.
As lawyers we have a duty to our clients to get it right from the outset. There is no point in taking a case to trial with little prospect of success because you cannot properly explain highly technical evidence to a judge in such a way as to convince him of the perpetrators guilt, beyond reasonable doubt. Equally, the accused has a right to a fair trial and that means we have to be able to challenge technical evidence which clearly does not support the charges faced by the accused.
Our specialist cybercrime lawyers have handled many cases involving ‘cybercrime evidence’. The major advantage our team of lawyers have over many other advocates is instant access to our in-house computer forensics team. They are on hand to help us understand the subject matter of these cases, deliver expert reports, assist with our examination in chief, cross examination and give testimony to assist the court to make sense of complicated evidence. All of this is key to a successful prosecution or defence.
About the Authors:
Mr. Andrew Smith (Andy) – Director of Computer Forensics Services at Orion Forensics Thailand
Andrew has 17 years’ experience in the field of digital forensics. Andrew was a UK police officer for 9 years of which the last 4 years was spent working within the police computer crime unit where he received extensive forensic training. His role included the acquisition of electronic data, analysis and the presentation of evidence in the UK courts as an expert witness.
Andrew has now been based in Bangkok for over 7 years and is the Director of Computer Forensics Services for a commercial investigation company called Orion Investigations. His role is to oversee all forensic investigations, business development, promote awareness of cyber security and present evidence as an expert witness in Thai courts. He has regularly appeared as a guest speaker for various business chambers and organizations. Andrew has developed a range of forensic training courses for the local Thai market. Andrew has also developed a number of free forensic tools which are now used in forensics labs all around the world.
Email: andrew@orioninv.co.th
Electronic Data Acquisition and Analysis Service
Read More
Dealing with Cyber Crime – Would your business know how to respond
They say there are two certainties in life, death and taxes. I would suggest that there are now three. Death, taxes and being confronted with cybercrime. It is not uncommon to hear the phrase cybercrime or cyberterrorism being used in the media and how another major company has been hacked. Yet many people are still unsure exactly what constitutes cybercrime and whether they may have been a victim.
Read MoreTurning to the Dark Side – The Dangers of Using Mobile Devices for Business
Turning to the Dark Side – The Dangers of Using Mobile Devices for Business With the introduction of the iPad in 2010, the tablet quickly emerged as one of the fastest selling devices in history. Tablets have achieved a level of adoption in 3 years that took smartphones nearly 10 years to achieve. In 2013, the adoption of smartphones in the US surged to 64 % according to the latest Nielsen survey.
Read More
Using Digital Evidence in Thai Courts
Introduction Computer forensics or digital forensics as it is now commonly called, is still in its infancy in Thailand but that is about to change. For the past two years I have regularly searched on the keywords “computer forensics Thailand.
Read More
